Combining Security and Ease: Cloud Access Security Brokers (CASBs)
Key Takeaways
- Understanding the role of CASBs in today’s cloud-centric world.
- How CASBs contribute to data security and regulatory compliance.
- Real-world applications and benefits of using a CASB.
- Key features to look for when choosing a CASB.
The Rise of Cloud Access Security Brokers
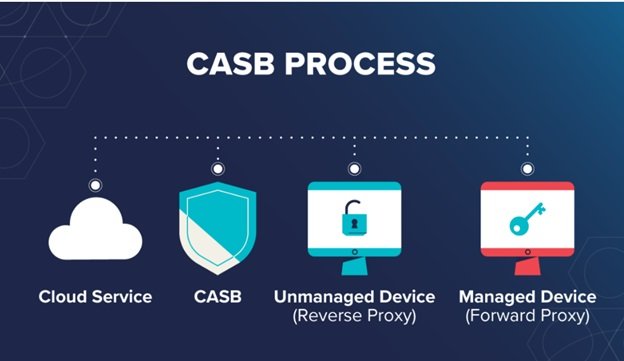
In a world where cloud computing is becoming increasingly dominant, the need for robust security measures is more critical than ever. This is where a Cloud Access Security Broker (CASB) comes into play. CASBs act as gatekeepers, providing a secure layer between cloud service users and applications. They ensure that the organization’s security policies are extended into the cloud environment. By monitoring user activities and enforcing security policies, CASBs help mitigate the risks associated with cloud services, thus offering peace of mind to IT managers. With the rise of remote work, more companies are moving their operations to the cloud. However, this migration has made them vulnerable to many security threats, such as data breaches, unauthorized access, and malware attacks. CASBs address these concerns by offering a centralized point of control over cloud usage, ensuring that sensitive data remains protected. They serve as the last line of defense, ensuring that data exchanged between on-premises and cloud environments meets the highest security standards.
The Role of CASBs in Data Security
CASBs offer an array of security measures to protect user data in cloud environments. These include encryption, access controls, and threat detection capabilities. For instance, CASBs help organizations ensure that sensitive data remains encrypted during transit, preventing unauthorized access. Data encryption is not just a “nice-to-have” feature; it’s crucial for maintaining the confidentiality and integrity of sensitive information. Encryption is essential for organizations dealing with sensitive information, such as financial or personal health information. By maintaining strong encryption standards, CASBs make it significantly harder for cybercriminals to intercept and read sensitive data. This functionality is essential for safeguarding intellectual property and meeting data privacy regulations. Encryption, when properly implemented, ensures that even if data is intercepted, it cannot be read or misused by malicious actors.
Ensuring Regulatory Compliance
One of the lesser-known but equally critical roles of CASBs is their ability to help organizations maintain regulatory compliance. In industries such as finance and healthcare, adhering to regulations like GDPR and HIPAA is non-negotiable. CASBs can automatically enforce compliance policies, reducing the risk of costly fines and reputational damage. As a result, compliance teams have less administrative work to undertake, freeing them up to concentrate on strategic projects rather than being weighed down by tedious procedures. In addition to automating policy enforcement, CASBs provide comprehensive reporting features. During audits, these reports help prove to corporations that they conform to numerous regulations. This automated and methodical approach simplifies what would otherwise be a difficult and time-consuming process. Having current and accurate compliance reports facilitates audits and increases the organization’s reputation and dependability with clients and authorities
Real-World Applications of CASBs
Numerous companies are now relying on CASBs to address their cloud security requirements. For instance, consider a financial firm that must safeguard sensitive information while enabling staff to utilize cloud platforms. By implementing a CASB, they can supervise and manage data access, ensuring that only approved personnel have access to sensitive information. This degree of supervision is crucial to uphold the confidence of their customers, who anticipate their financial information to be treated with the highest level of consideration. Cloud-based services are being utilized more in schools for teaching and administration purposes. A CASB can control access to these services, guaranteeing the protection of student data and ensuring compliance with privacy regulations such as FERPA. Collecting and storing sensitive information, ranging from student grades to personal identification details, is especially crucial for educational institutions.
Benefits of Using a CASB
Employing a CASB has several advantages. Businesses may benefit from easier compliance reporting, improved cloud activity visibility, and improved data security. Additionally, CASBs can offer comprehensive analytics and logs, which help IT teams react quickly to security concerns. This degree of visibility is priceless when it comes to seeing possible risks before they materialize into serious security breaches. Thanks to this increased visibility, organizations are able to identify unusual patterns of behavior that may indicate a security problem or data breach. Early detection of these dangers enables firms to reduce risks before they cause significant harm. For instance, an unexpected increase in data download activity would point to an effort to steal confidential information, in which case the IT staff would take quick action.
Key Features to Look For in a CASB
When selecting a CASB, focus on essential features such as data encryption, threat detection, and compliance enforcement. Additionally, consider a CASB that offers seamless integration with existing security frameworks and cloud service providers. For further insights, check out this in-depth CASB guide on TechTarget. Sustaining a uniform security posture in on-premises and cloud settings requires seamless integration. In addition to technological aspects, user interface design and deployment simplicity are crucial. Without needing IT workers to undergo intensive training, a CASB should be simple to administer. Seek a system that offers thorough, readable reports and user-friendly dashboards. Interfaces that are easy to use can help firms immediately discover the benefits of their CASB solution by lowering the learning curve.
Conclusion
Cloud Access Security Brokers have become indispensable for organizations leveraging cloud services. They provide crucial security functions, ensure compliance, and offer insight into cloud activities. By choosing the right CASB, organizations can confidently navigate the complexities of cloud security and protect their valuable data.
Read More: Top-Notch Security System Services For Ultimate Protection: Improve Your Home & Business Safety